|
Save/Close
|
Saves any changes and closes the Security screen. |
|
Print
|
Prints a report showing the contents of the Security Database, inluding Name, Email address, Password, User Code and each authorised user's Acess Rights. |
|
Add User
|
Used to add a new record to the security database |
|
Delete
|
Removes the current user from the security database |
|
First
|
Jumps to the FIRST user in the Security database |
|
Previuos
|
Reverses to the next previous user in the Security database with each click |
|
Next
|
Jumps to the next user in the Security database with each click |
|
Last
|
Jumps to the LAST user in the Security database |
|
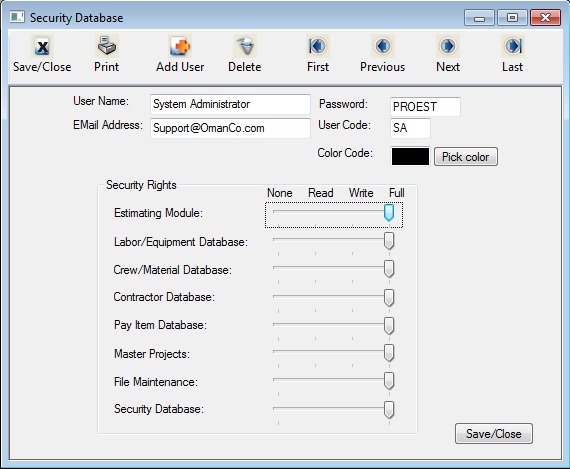
User Name
|
This field is the Name of the User. |
|
Password
|
This is the user's password. The password is a six-character field (maximum) that can contain either letters or numbers or both. The password is NOT case sensitive. (Note: NO TWO users can have the same password.)
|
|
User Code
|
This field is used to enter a two-character code for the current user(e.g. the users initials) . This code is used in the network version to identify users of the system. This two-digit code will be added to all task names within a job to identify the estimator who created the task. This is useful in a network environment where multiple estimators are working on a single job. This field is not required in the single user version but can be used if desired.
|
|
Email Address
|
This field is used to enter the user's email address. The email address is used within the system as the reply address when you send error messages or emails to Oman Systems.
|
|
Security Rights
|
These fields show all of the modules within the program. Access can be controlled to each one of these modules by sliding the pointer for each module. There are four available levels of access for each module:
| None |
No Access |
| Read |
Read Only |
| Write |
Read, Edit, Print |
| Full |
Read, Edit, Print, Delete, Add |
Note: There is no separate module displayed for the “Program Preferences.” Access to the Program Preferences Module is “controlled by” the access setting to the Security Module. To have access to the Program Preferences screen, the Security Database Module must be set to FULL.
|
|
Close
|
Pressing the CLOSE button will save any changes you made and close the Security Database window. |